Bye, Janet
Yesterday, I shared a tragic story from the Washington Post on LinkedIn. The story profiled several federal workers experiencing loss as a result of the administration's desire to put them 'in trauma'—some of whom went on to take their own lives. As one of the tens of thousands of workers referenced in the article, I shared the story as an example of the unprecedented challenges facing federal workers right now. I also shared it to highlight the challenge this poses to Americans writ large, many of whom don't see the connection. Within moments I received a comment that sought to appeal to my need to find new employment, but it was not what it seemed.
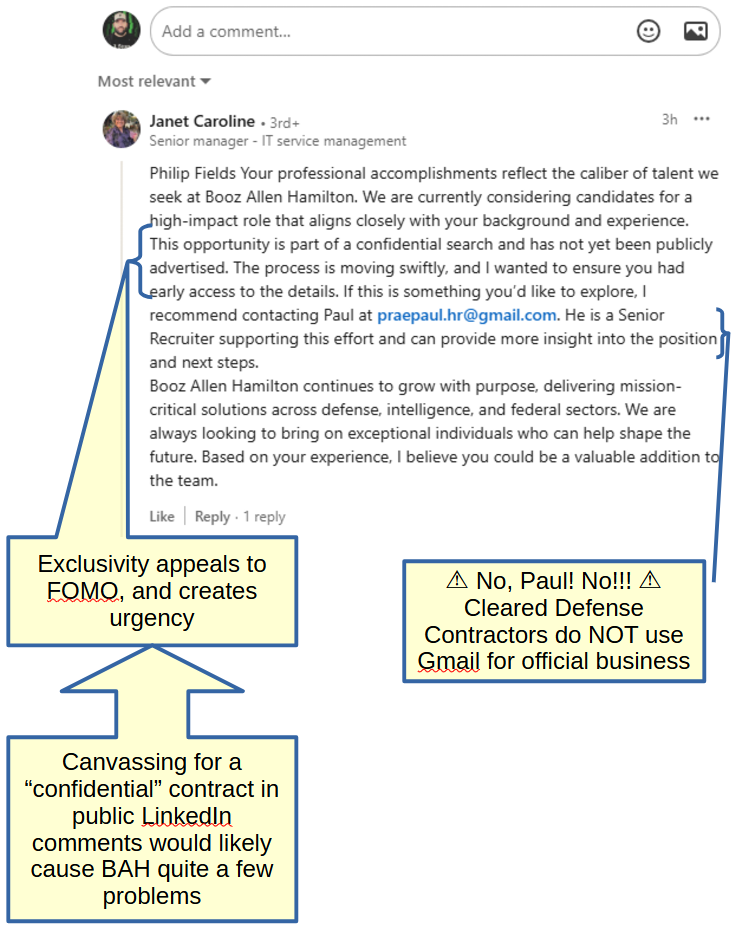
![A LinkedIn comment that reads, "Philip Fields Your professional accomplishments reflect the caliber of talent we seek at Booz Allen Hamilton. We are currently considering candidates for a high-impact role that aligns closely with your background and experience. This opportunity is part of a confidential search and has not been publicly advertised. The process is moving swiftly, and I wanted to ensure you had early access to the details. If this is something you'd like to explore, I recommend contacting Paul at praepaul.hr[at]gmail[dot]com. He is a Senior Recruiter supporting this effort and can provide more insight int the position and next steps. Booz Allen Hamilton continues to grow with purpose, delivering mission-critical solutions across defense, intelligence, and federal sectors. We are always looking to bring on exceptional individuals who can help shape the future. Based on your experience, I believe you could be a valuable addition to the team.](https://hax4libre.com/content/images/2025/05/Screenshot-2025-05-20-095129.png)
This commenter was an obvious spam bot. I should have blocked them, reported them, and gone on with my day. But after spending more than a decade staying silent online and quietly forwarding things like this on to the appropriate investigators, I wanted to try out my newfound freedom out and tell Janet to shove it. So, I initially responded with a tone that LinkedIn frowns upon. (Seriously, for a little bit there, Janet totally killed the vibe of an already very dark topic.)
I also did a little digging though. No, I didn't accidentally stumble in to a secret cabal of foreign intelligence officers plotting to destroy America. (We're doing a pretty good job of that ourselves right now.) That's up to the folks at LinkedIn and Google to sort out. Instead, I just wanted to get a sense of what Janet's game was. Why she thought I'd be dumb/desperate enough to bite, and what else she was up to. I'd also like to walk through some of that for folks who may look at the above comment and wonder why I'm being such a jerk to someone trying to help me out.
Let's start with the initial message and what set off the alarm bells first. I've called out a few things below. Most notably, no recruiter or senior manager should EVER be using a personal Gmail account for company business, especially not a cleared defense contractor like Booz Allen Hamilton. Did we learn nothing from #SignalGate? But let's look beyond that, because some people legitimately learned nothing from #SignalGate. Yes, Janet tries to appeal to my ego, but that's not all that different from a normal recruiter. No, the biggest red flag here is the air of exclusivity and sense of urgency Janet is trying to impress upon me. Janet needs me to get excited and turn my thinking brain off long enough to accept Paul into my circle of trust. This is pretty typical spammer stuff, but she also breaks another rule. A real cleared defense contractor would never so brazenly divulge sensitive details of a potential bid so openly on LinkedIn. That's a sure-fire way to lose a contract.
So, why wouldn't Janet just ask me to DM her for details instead? Or, why not just DM me first instead? I'm reading the tea leaves a bit here, and there's room for error, but let's give it a shot.
- The Obvious – It's expensive to DM strangers on LinkedIn.
- The Cutout – Janet's job is simple. She casts a wide net but only needs to succeed a few times. Janet sent this same form template comment to twelve people in the span of an hour. She's racing against the clock, knowing that LinkedIn is going to find her and shut her down. Paul, on the other hand, is stable. Paul's a pro. Paul monitors his email address waiting for Janet's bait to set.
- This handoff serves an added benefit though. If I continue to work with Janet, there's a high likelihood that over time she's going to ask me to do something that's just a little off, but I'll always remember the odd way she contacted me in the first place. Paul is clean though. Paul is "clearly" (sarcasm, folks) a trusted insider. If Janet can pass me to Paul with minimal hiccups, then I'm much less likely to question whatever odd thing Paul asks me to do the first time. And Paul won't be the last in this chain either. Paul will inevitably hand me off to a hiring manager, and several other "people" who will all take their pound of flesh, while drawing me into a network large enough that my ego won't let me believe that it could all be fake.
- The Bona Fides – In the unlikely event Janet doesn't get burned in the first 24 hours, she'll inevitably want to continue her unsavory networking scheme. When she operates in public comments, she builds a trail of bona fides she can refer back to just like that door-to-door pest control guy who just signed up three of your neighbors and is now offering you the same great deal. She will inevitably try to use you as a reference in the future to lure some other poor soul in.
But that's a lot to read into one comment. Let's look at the rest of Janet's profile, and see if we can figure out 'why me' and 'what else.' At first glance, I can only assume that Janet must be new, but not in the 'obviously new to LinkedIn' kind of way. I've got no room to judge there. Janet is new to the entire field of social engineering. Like a serious amateur. As a matter of fact, Janet, if you're reading this please dust off your resume and get on LinkedIn for real. You need to find a new line of work.
When a "senior manager" of any kind gets on LinkedIn and doesn't immediately connect with every other Boomer and GenXer on LinkedIn, you know something is up. There is zero percent chance of Janet having zero followers and being legit. Life just doesn't work that way. And no, LinkedIn doesn't allow you to hide your follow count like some other social networks. This lady legitimately has no friends. 😿
She also has no verification badges. Honestly, that's a lot of y'all, and y'all need to fix that, but in this case it's for an obvious reason. Janet doesn't work at Booz Allen, and that's not her real name. The last thing is the most interesting to me though. Janet was banging out templated comments at the cyclic rate, like she knew she had one job on this Earth and a limited amount of time to get it done. Janet was racing the LinkedIn censor clock.
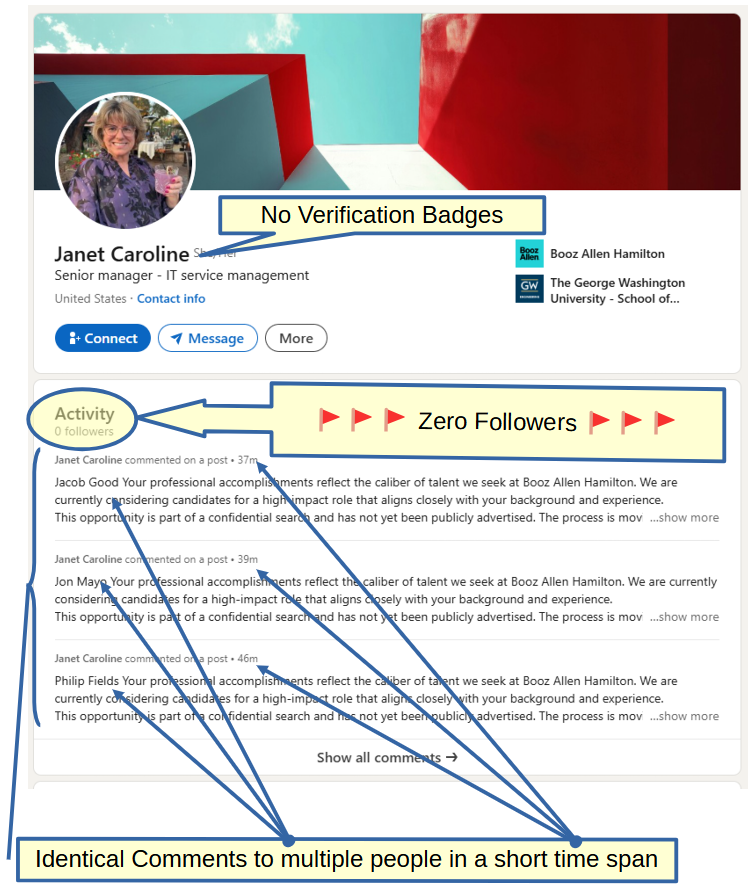
I did expand the rest of Janet's comments to see how far back her history goes. She spammed about twelve different people with the same comment approximately an hour. There was no other activity. All of the recipients appeared to be from the United States or the United Kingdom, and all had backgrounds in the defense industry. Shocking. I know. The timing and target of the comments is what really stuck with me here. At first, I suspected this to be an actual bot doing automated spam, but this appears more like an actual hands-on-keyboard human clicking through posts looking for targets.
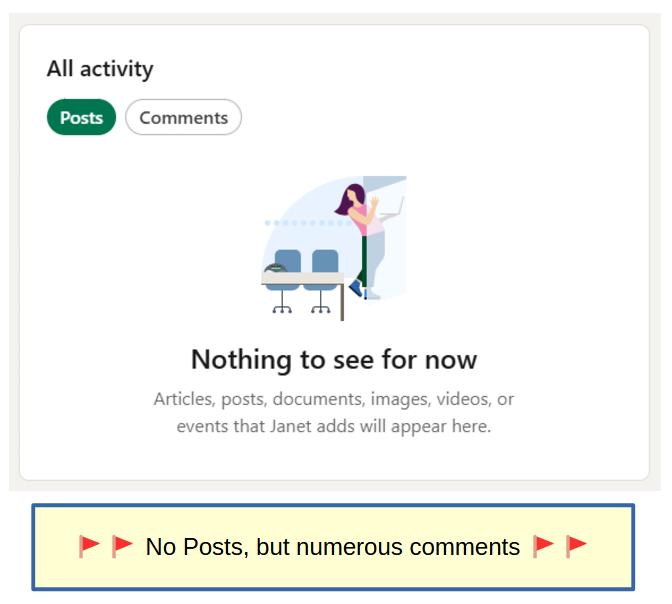
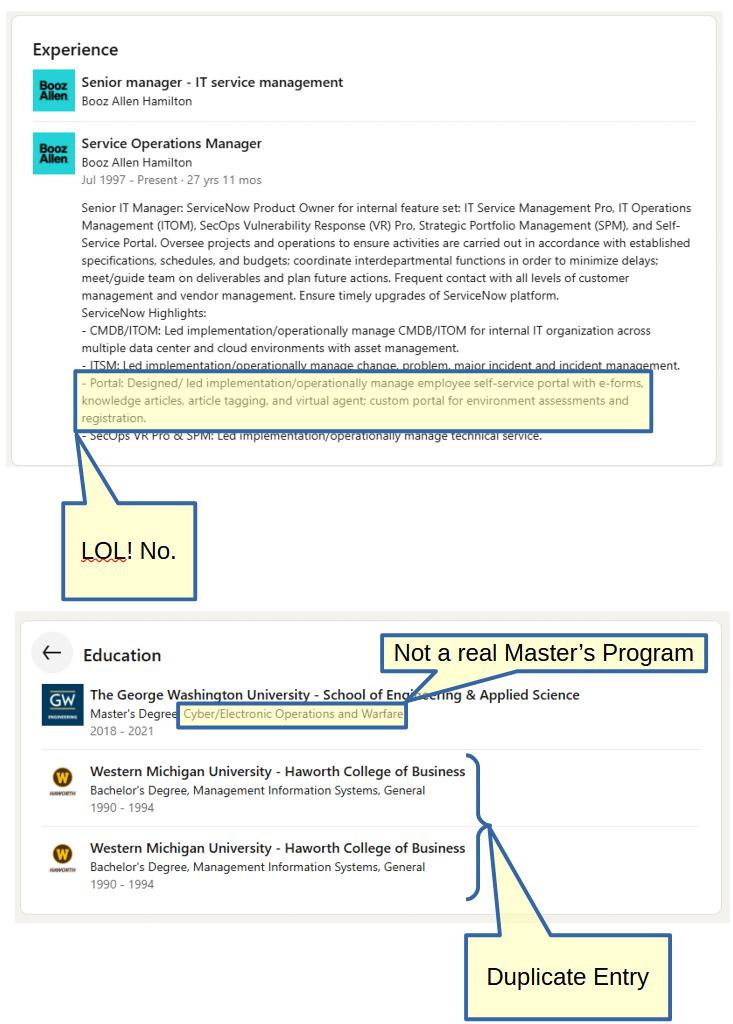
Janet's education and experience weren't particularly telling. I don't know enough about ServiceNow to know whether any of the below sounds fabricated, but there were a couple other minor issues that could be equal parts 'someone who didn't think through their legend' and 'someone who just didn't proofread.' If anyone would care to weigh in on the legitimacy of her alleged Master's Degree I'd love to hear about it, but from what I could tell on GW's site, that's fake. The typos and duplicative entries were also just too basic to let go.
Finally, let's talk about that face. No, I'm not going to bash the woman in the photograph's looks. That would be cruel, and she's probably a lot of fun. But her name ain't Janet. When I first blew up the image, I expected the tell-tale signs of an AI-generated image, but I was pleasantly surprised. She's got normal fingers and natural reflections that give off that 'I'm a legit human' vibe. Moreover, this place is real. For all intents and purposes, this appears to be an actual human enjoying one of LON's Last Drop cocktails at the Hermosa Inn in Paradise Valley, Arizona. The glassware and straws even match what I was able to find on Yelp and TripAdvisor. I took a guess at where she was sitting for funsies, but that doesn't help much.

Just to hammer home the above, as an OSINT aside, with a little help from a few image search engines I was able to find this spot using the distinct fountain, mature mesquite tree, and a few cacti in the background. NOTE: A lot of the responsible reverse image searches don't like to look for people anymore. You'll have much better luck if you crop your images down to just the distinct background features and go from there. In this case, the top right quarter of the image was all I needed to find dozens of photos of the right patio.
I did not find the source of the original photo, but I also didn't search social media platforms such as Facebook, Instagram, etc. At some point, you have to draw the line between curiosity and professional interest, and in this case it wasn't worth the extra effort. My assumption is that the photo was likely stolen off of some poor woman's vacation reel. If anyone wants to track her down and let her know that Janet is making her look like an amateur on LinkedIn, be my guest. She looks a little feisty, and I think she could take Janet.
That pretty much sums things up. I haven't finished putting together my full OSINT toolbox yet, so I'm sure there are plenty of things I missed. For instance, I only ran Paul's email through a handful of surface level search engines and came up empty. I'd be very surprised if he doesn't have at least a couple of accounts registered on that Gmail though. So, what did we learn?
Based on the targets' defense backgrounds in the US and UK, and the use of a human for the spamming, I'd venture to guess this is some foreign intel officer who also read the Foundation for Defense of Democracies paper highlighting Chinese targeting of recently laid off government employees and thought that sounded like a great idea. Unfortunately for them, they didn't have the budget or training to do a remotely decent job. But again, that's up to the hardworking trust and safety folks at Google and LinkedIn to figure out now.

Better luck next time, Janet.
